Prevent your sensitive data from being stolen and make your applications faster. Whereas private MPLS services provided enterprise wide area networks (WANs) with some inherent protection, no such assurances are true of the Internet. All enterprise data going to and from the cloud must be encrypted.
Silver Peak’s Unity architecture protects data in flight with high-performance, edge-to-edge encryption without complex configuration or performance degradation.
Silver Peak's Accelerated IPSec, site-to-site VPN dramatically improves network performance, takes minutes to install, and is included in every one of Silver Peak's award-winning, WAN acceleration products. With Accelerated IPSec, enterprises benefit from:
- Enterprise class security provided through AES-256 encryption and SHA-1 authentication.
- Accelerated site-to-site performance that is as much as 98x faster than conventional VPNs.
- Significant capital savings by avoiding the purchase of additional VPN hardware.
- Easy deployment requiring no networking expertise or painstaking tunnel configuration.
- Securing all applications even when they are passed-through by the Silver Peak software.
- Instant access by download from the Silver Peak software marketplace.
Accelerated Encryption is available today and is just one more example of Silver Peak's commitment to value. See for yourself by downloading a Silver Peak software appliance for free from our software marketplace.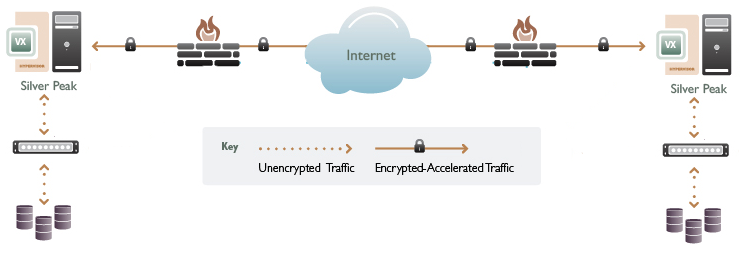
Featured Products
-
Unity Architecture: Building an SD-WAN Fabric
Silver Peak Unity is the premier solution for broadband and hybrid WANs.
-
VX Virtual WAN Optimization Software
Silver Peak VX WAN optimization software supports the full list of Silver Peak WAN optimization features. Use Silver Peak VX software to build a Silver Peak Unity WAN fabric for integrating your enterprise WAN, the Internet and the cloud, and to optimize every SaaS application.
-
NX Appliances for Application Acceleration and Replication Acceleration
Silver Peak NX WAN optimization appliances are the industry's highest-performance WAN optimization solutions, delivering three-times the WAN performance and capacity of the nearest competing products. Silver Peak Software for Life program means you can convert NX appliances to VX software at anytime for free.
Resources
-
Growing concern over the interception of Internet traffic by governmental agencies is driving enterprises to revisit how they secure storage replication and other essential applications between locations. Conventional site-to-site virtual private networks (VPNs) protect data in-flight, but require extensive networking expertise to configure and do not address the performance challenges of delivering applications over distance. Silver Peak's Accelerated IPSec combines the best of site-to-site IPSec VPN security and wide area network (WAN) acceleration.
-
Learn how Regional Medical Center deployed Silver Peak and gained 10x improvement (average) in application performance across the WAN
-
Charlotte Metro Federal Credit Union (CMCU) was struggling to replicate all of its data to a disaster recovery location within its Recovery Point Objective (RPO). Branches were also growing, putting pressure on CMCU to upgrade their T1 lines. By deploying Silver Peak software at each location, CMCU not only met its RPO and avoided line upgrades, but also protected data with Silver Peak’s built-in Accelerated IPSec VPN. “We reduced our costs, improved our performance and secured our data,” says David Cooper, vice president of information systems at Charlotte Metro. “I couldn’t ask for anything more from a VPN.”
-
When Citizens Business Bank needed to fulfill a disaster recovery initiative, virtual WAN optimization software was the logical choice. The company had already virtualized its data center and even after more than doubling the bandwidth from their data center to their disaster recovery (DR) location, data replication still took 8-times too long.
-
Internet Protocol Security (IPSec) is a standard set of protocols describing how to ensure the authenticity, privacy, and integrity of data in transit. A Virtual Private Network (VPN) secures traffic between locations as well as if the traffic was within a location.
-
Encrypting SharePoint traffic, or for that matter any client-server traffic is even more important today than before; users work beyond the security of corporate walls while more security threats originate from within them. But encryption algorithms also cause problems by rendering application traffic largely immune to deduplication algorithms. Companies can end up with a secure application that responds like a slug over long distances.