Step 6: Verify an Access List
Access lists are used to match traffic for processing by a specific overlay.
Best practice is to:
- Create an ACL for real-time traffic to map onto the real-time overlay.
- Create a default ACL to catch all other traffic.
To create an access list:
-
Go to Configuration > Access Control Lists.
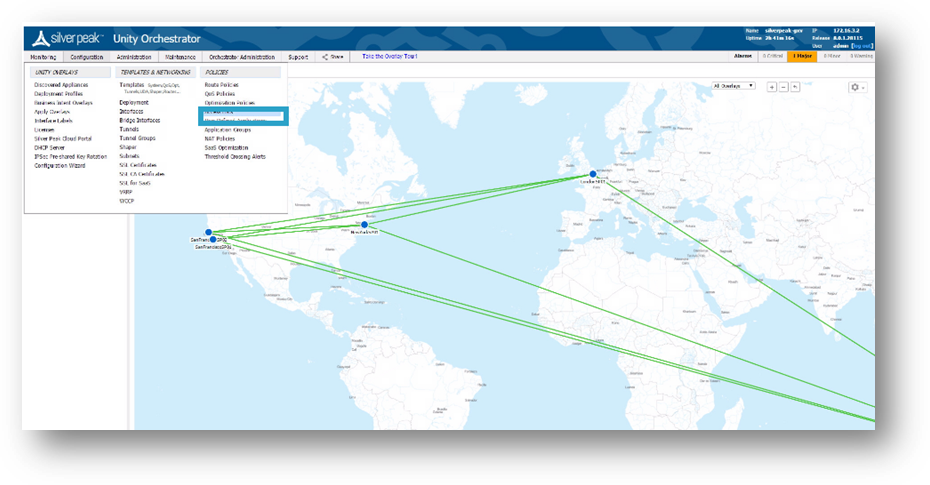
Figure 8. Access Control List
-
Click Manage Access Lists with templates.
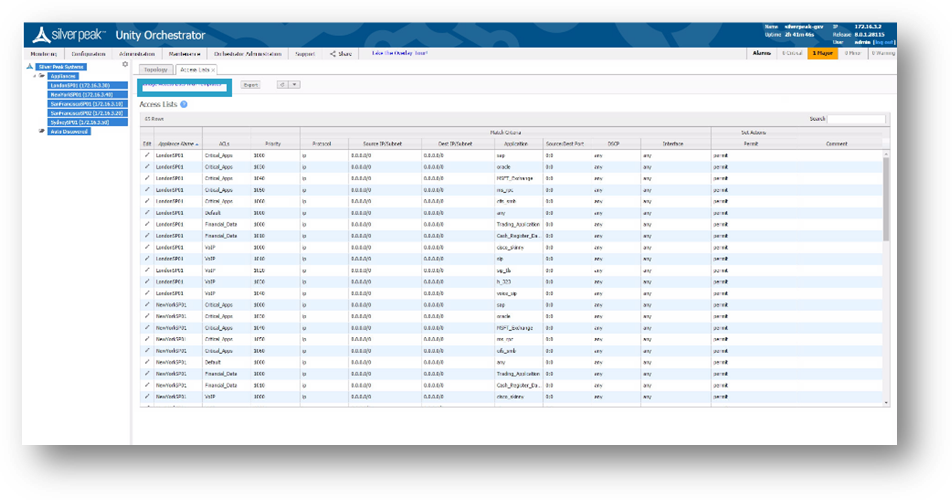
Figure 9. Manage Access Lists with Templates
-
Several Default Access-Lists are already created:
- Realtime – voice and video protocols.
- Interactive – citrix, terminal services, RDP etc.
-
AnyTraffic – default permit ip any any.
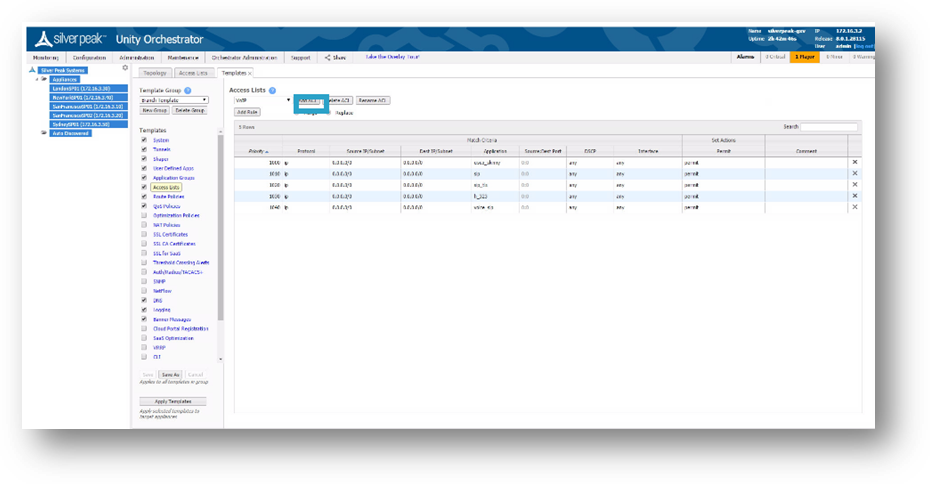
Figure 10. Access Control List Template
- Make your changes, then click Save.