|
n
|
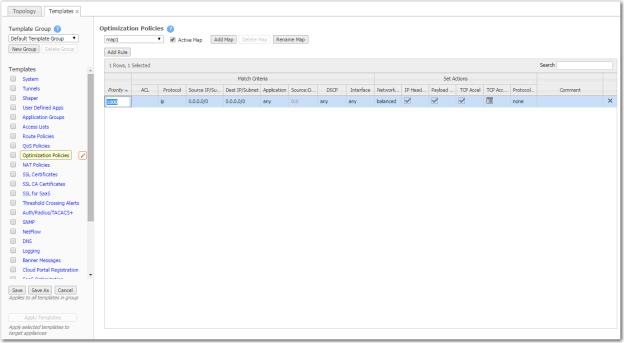
With this template, you can create rules with priority from 1000 – 9999, inclusive. When you apply the template to an appliance, the Orchestrator deletes all appliance entries in that range before applying its policies.
|
|
n
|
If you access an appliance directly (via the WebUI or the command line interface), you can create rules with higher priority than Orchestrator rules (1 – 999) and rules with lower priority (10000 – 65534).
|
|
n
|
To allow any IP address, use 0.0.0.0/0.
|
|
n
|
|
n
|
|
n
|
Network Memory addresses limited bandwidth. This technology uses advanced fingerprinting algorithms to examine all incoming and outgoing WAN traffic. Network Memory localizes information and transmits only modifications between locations.
|
|
•
|
Maximize Reduction optimizes for maximum data reduction at the potential cost of slightly lower throughput and/or some increase in latency. It is appropriate for bulk data transfers such as file transfers and FTP, where bandwidth savings are the primary concern.
|
|
•
|
Minimize Latency ensures that Network Memory processing adds no latency. This may come at the cost of lower data reduction. It is appropriate for extremely latency-sensitive interactive or transactional traffic. It's also appropriate when the primary objective is to fully utilize the WAN pipe to increase the LAN-side throughput, as opposed to conserving WAN bandwidth.
|
|
•
|
Balanced is the default setting. It dynamically balances latency and data reduction objectives and is the best choice for most traffic types.
|
|
•
|
Disabled turns off Network Memory.
|
|
n
|
IP Header Compression is the process of compressing excess protocol headers before transmitting them on a link and uncompressing them to their original state at the other end. It's possible to compress the protocol headers due to the redundancy in header fields of the same packet, as well as in consecutive packets of a packet stream.
|
|
n
|
Payload Compression uses algorithms to identify relatively short byte sequences that are repeated frequently. These are then replaced with shorter segments of code to reduce the size of transmitted data. Simple algorithms can find repeated bytes within a single packet; more sophisticated algorithms can find duplication across packets and even across flows.
|
|
n
|
TCP Acceleration uses techniques such as selective acknowledgements, window scaling, and maximum segment size adjustment to mitigate poor performance on high-latency links.
|
|
n
|
Protocol Acceleration provides explicit configuration for optimizing CIFS, SSL, SRDF, Citrix, and iSCSI protocols. In a network environment, it's possible that not every appliance has the same optimization configurations enabled. Therefore, the site that initiates the flow (the client) determines the state of the protocol-specific optimization.
|
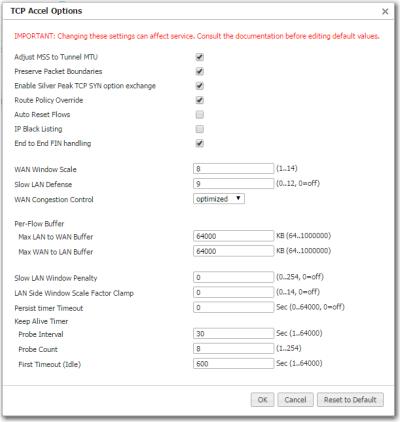
CAUTION  Because changing these settings can affect service, Silver Peak recommends that you do not modify these without direction from Customer Support.
Because changing these settings can affect service, Silver Peak recommends that you do not modify these without direction from Customer Support.
|
This feature is enabled by default so that the maximum value of the end host MSS is always coupled to the Tunnel MSS. If the end host MSS is smaller than the tunnel MSS, then the end host MSS is used instead.
|
|||||||
|
NOTE: Whether this feature is enabled or not, the default behavior when a tunnel goes Down is to automatically reset the flows.
|
|||||||
|
|||||||
|