Use this template to add NAT map rules to all the appliances that support Network Address Translation.
|
1
|
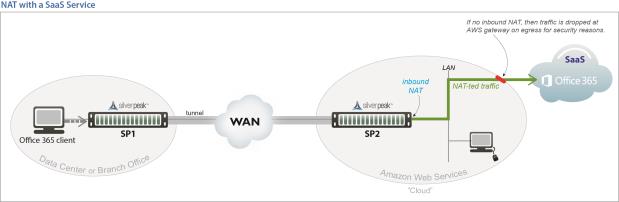
Inbound NAT. The appliance automatically creates a source NAT (Network Address Translation) map when retrieving subnet information from the Silver Peak Cloud portal. This ensures that traffic destined to SaaS servers has a return path to the appliance from which that traffic originated.
|
|
2
|
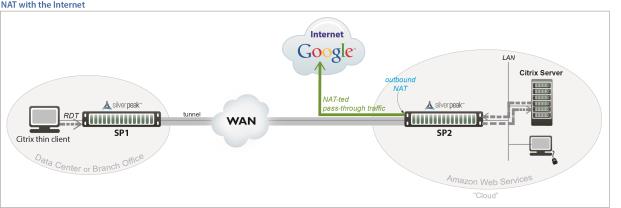
Outbound NAT. The appliance and server are in the cloud, and the server accesses the internet. As in the example below, a Citrix thin client accesses its cloud-based server, and the server accesses the internet.
|
For deployments in the cloud, best practice is to NAT all traffic — either inbound (WAN-to-LAN) or outbound (LAN-to-WAN), depending on the direction of initiating request. This avoids black-holing that can result from cloud-specific IP addressing requirements.
|
n
|
Enabling NAT all applies NAT policies to pass-through traffic as well as optimized traffic, ensuring that black-holing doesn't occur. NAT all on outbound only applies pass-through traffic.
|
|
n
|
If Fallback is enabled, the appliance moves to the next IP (if available) when ports are exhausted on the current NAT IP.
|
The appliance can perform source network address translation (Source NAT or SNAT) on inbound or outbound traffic.
|
n
|
Dynamic – created automatically by the system for inbound NAT when the SaaS Optimization feature is enabled and SaaS service(s) are selected for optimization. The appliance polls the Silver Peak Unity Cloud Intelligence service for a directory of SaaS services, and NAT policies are created for each of the subnets associated with selected SaaS service(s), ensuring that traffic destined for servers in use by those SaaS services has a return path to the appliance.
|
|
n
|
Manual – created by the administrator for specific IP addresses / ranges or subnets. When assigning priority numbers to individual policies within a NAT map, first view dynamic policies to ensure that the manual numbering scheme doesn't interfere with dynamic policy numbering (that is, the manually assigned priority numbers cannot be in the range: 4000-5000). The default (no-NAT) policy is numbered 65535.
|
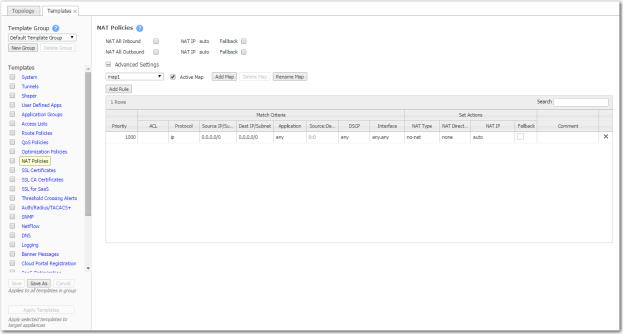
The NAT policy map has the following criteria and Set Actions:
|
•
|
To allow any IP address, use 0.0.0.0/0.
|
|
•
|
|
•
|
|
n
|
|
•
|
no-nat is the default. No IP addresses are changed.
|
|
•
|
source-nat changes the source address and the source port in the IP header of a packet.
|
|
•
|
inbound NAT is on the LAN interface.
|
|
•
|
outbound NAT is on the WAN interface.
|
|
•
|
none -- the only option if the NAT Type is no-nat.
|
|
n
|
|
•
|
auto -- Select if you want to NAT all traffic. The appliance then picks the first available NAT IP/Port.
|
|
•
|
tunnel -- Select if you only want to NAT tunnel traffic. Applicable only for inbound NAT, as outbound doesn't support NAT on tunnel traffic.
|
|
•
|
[IP address] -- Select if you want to make NAT use this IP address during address translation.
|
|
n
|
Fallback -- If the IP address is full, the appliance uses the next available IP address.
|