|
n
|
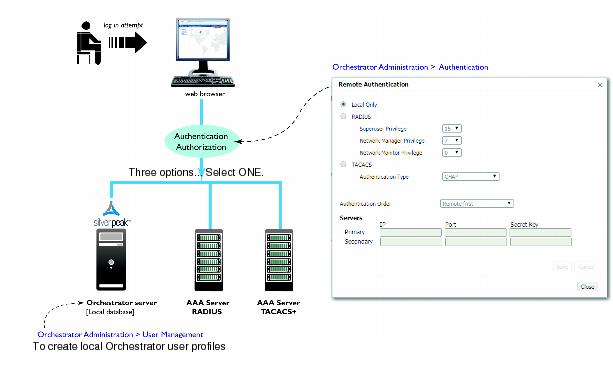
The AAA server (Authentication Authorization Accounting server) can be either a RADIUS server or a TACACS+ server.
|
|
n
|
Add users to the Orchestrator server’s local database via the Orchestrator client’s Orchestrator Administration > User Management menu. The user profile includes the user role, which maps to a particular level of authorization and determines what the user can do.
|
|
n
|
The Orchestrator has three user roles: Admin Manager (Superuser), Network Manager, and Network Monitor. Authorization always maps to one of these three levels:
|
|
•
|
Admin Manager has all privileges. It’s the equivalent of Superuser.
|
|
•
|
Network Manager has read/write privileges. In practice, these are the same privileges that Admin Manager has.
|
|
•
|
Network Monitor has view-only privileges.
|
|
•
|
If Local Only is selected, then authentication defaults to the Orchestrator server’s local database.
|
|
•
|
|
•
|
|
•
|
|
n
|
The Secret Key enables the Orchestrator to talk to the access control server. The Orchestrator has hard-coded keys for TACACS+, so no user entry is required.
|